In today’s digital landscape, secure dedicated server hosting with robust DDoS protection is essential for safeguarding high-traffic websites and mission-critical applications.
As cyber threats evolve, businesses face volumetric, protocol, and application-layer attacks that can disrupt operations and compromise data integrity. This comprehensive guide demystifies DDoS defense strategies, offering actionable insights into traffic filtering, rate limiting, and advanced firewall implementations.
By exploring top-rated providers and integration best practices, readers gain the tools needed to fortify their online defenses and ensure uninterrupted service.
Embrace enterprise-grade security to protect your reputation and maintain customer trust. Empower your infrastructure with proactive, intelligent, comprehensive protection.
DDoS Protection Overview
Why You Need DDoS Protection
No one wants their website or online services to be disrupted, right? That’s exactly what a Distributed Denial-of-Service (DDoS) attack aims to do—create chaos by overwhelming your server with unwelcome traffic.
If you’re running a high-traffic site or managing an IT operation, you’ve gotta have DDoS protection on lockdown. Without it, you might find yourself with unhappy customers, lost revenue, and a reputation that’s slipped on a banana peel Cloudflare.
Secure and powerful dedicated server hosting with top-notch DDoS protection is crucial for keeping things ticking over nicely. Imagine your servers get hit with an attack, leaving customers in the dark. Not good, right? You need to shield your online services to avoid a business nightmare Liquid Web.
Different Flavors of DDoS Attacks
DDoS attacks aren’t a one-size-fits-all thing, oh no! Here’s what you might face:
- Volumetric Attacks: These guys slam your network with traffic, gobbling up bandwidth like there’s no tomorrow.
- Protocol Attacks: They mess with network rules, turning your server into chaos central by overloading it with dummy requests.
- Application Layer Attacks: These nasties go straight for web apps, peppering them with requests until legitimate users are locked out.
| Type of Attack | How It Hits | The Mess It Causes |
|---|---|---|
| Volumetric Attacks | Overwhelming traffic | Steals your bandwidth |
| Protocol Attacks | Breaks network protocols with requests | Drains server resources |
| Application Layer Attacks | Bombards web apps with requests | Leaves services hanging |
The baddies use something called botnets—a shadowy collection of infected gadgets—to hide their tracks. With computers and IoT devices recruited into their digital army, attacks pack a mean punch CISA.
As these attacks get sneakier and more potent, leaning on cloud-based DDoS protection becomes your digital shield. It tackles harmful traffic and keeps your operations humming smoothly. Treat DDoS protection like locking the door before you leave; it’s not just good practice, it’s a must-have Liquid Web.
To step up your game with dedicated server hosting and security, check out our dedicated server hosting guide or learn about top servers for bustling sites.
Choosing a DDoS Protection Provider
Picking the right DDoS protection company for your dedicated server hosting with DDoS protection is essentially about channeling your inner detective. You gotta look at different angles, and this guide is your trusty magnifying glass.
Factors to Consider
When searching for that perfect fit, you need to really know what makes your business tick. Here’s a breakdown of what to keep an eye on:
- Experience and Reputation: Dig into the company’s history. Has it been around the block a few times? Good reviews mean you might be able to sleep a little better at night.
- Variety of Protection: Does it offer a shield against all the nasty stuff like network and application attack layers?
- Scalability: As your business grows, can its services stretch and grow too?
- Integration Capabilities: Does it play nicely with your current setup, or do you need to fit a square peg into a round hole?
- Cost: Free might sound sweet, but sometimes, you get what you pay for. Weigh up your options.
- Customer Support: When stuff hits the fan, you need someone ready to help. Look for reliable support that’s got your back any time of day.
Cloud-Based DDoS Protection Services
Cloud-based services are like hiring a tech-savvy bodyguard – quick to jump in and handle trouble. Check out some big names:
- AWS Shield: This one’s got its eyes on your app 24/7, knocking those attackers for a loop. (eSecurity Planet)
- Cloudflare: These guys took on an enormous attack—71 million requests a second—and still walked away the champ in 2023.
- GCore: With real-time bot watching and top-tier firewall action, they’re ready to protect on all fronts.
- Azure DDoS Protection: Microsoft’s answer with built-in guardians for Azure-hosted apps.
- Vercara UltraDDoS Protect: A tag-team approach with hardware and cloud in the ring against complicated attacks.
Provider Evaluation Criteria
To make sure you’re picking wisely, here’s a checklist to keep you on track:
| Criteria | Description |
|---|---|
| Incident Response Time | How fast do they jump when there’s an attack? |
| Uptime Guarantee | Are they promising a rock-steady service with a solid SLA? |
| Global Coverage | Can they flex their muscles worldwide with loads of points of presence (PoPs)? |
| Customization Options | Can they cater to all your quirky security needs? |
| Performance Impact | Is there any slowdown or hiccup when their protection kicks in? |
| Reporting and Analytics | Do they offer detailed insights to help you dissect and understand threats and mitigate effectively? |
| Compliance | Do they line up with all those industry rules and checks that make your legal team happy? |
By peeking at these factors and checking those boxes, you can zero in on the DDoS protection provider that meets your company’s needs.
Curious about more ways to keep your dedicated server safe? Swing by our all-you-need-to-know dedicated server hosting guide. Check out our tips on dedicated server security best practices to toughen up your defenses too.
Risks of DDoS Attacks
Right, so DDoS (Distributed Denial of Service) attacks aren’t just digital myths. They’re real, and they’re absolute wreckers of online peace. Especially if you’re into dedicated server hosting with DDoS protection, you’ve got to be extra alert about what they could do to your online kingdom.
Impact on Online Services
Look, a DDoS attack isn’t just a bump in the road; it can totally mess up your online presence. We’re talking angry customers, revenue nosedives, and your reputation taking a hit. Our friends over at BuzzClan stress the big deal about having DDoS protection. Why? To keep your business rolling and dodge these cyber lemons.
Here’s what happens when a DDoS attack decides to rain on your parade:
- Service Downtime: Your site or app being offline is a fast track to customer frustration and financial wipeout.
- Cheesy Performance: Imagine everyone’s pinging your servers, slowing them down – it’s like asking a sloth to run a marathon.
- Ops Chaos: Your tech team will be running like headless chickens addressing issues instead of focusing on regular tasks.
Take a peek at this cold hard data on what these attacks can cost you:
| Parameter | Estimated Impact |
|---|---|
| Downtime cost/hour | $100,000 – $500,000 |
| Customer exit stage left | Up to 40% |
| Get-back-on-your-feet time | Takes a while – hours to days |
Need to beef up your defenses? Check out our article on dedicated server security measures.
Increasing Vulnerabilities with IoT
Now, IoT devices are everywhere and they’re making DDoS attackers’ jobs a walk in the park. Those gizmos that talk to each other and make life easier? Yeah, they’re also opening doors to hackers. The CISA says these little gadgets often get hijacked without anyone even batting an eyelid.
Watch out for these trouble spots with IoT gadgets:
- Busted Security: Many of these devices think passwords are optional – easy pickings for attackers.
- Network Open for Business: Once in, compromised devices can break through your network’s defenses for a mega DDoS attack.
- Bigger Whammy: With IoT devices multiplying like bunnies, they can supercharge a DDoS attack, leading to more chaos.
Locking down your IoT gadgets is a must to avoid these disasters. Secure them at both the gadget and network level, as per Liquid Web.
| Vulnerability | Risk Level | How to Keep It Locked Down |
|---|---|---|
| Lousy IoT Security | High | Go for strong passwords, frequent updates, and firewalls |
| Network Invites All | Medium | Cut the party short with network segmentation |
| Poor Monitoring | High | Have your eyes everywhere with continuous network traffic checks |
Want to stay a step ahead of DDoS attacks? Jump to our take on dedicated server security best practices.
Getting smart about DDoS risks and rolling out serious protection measures are your gold tickets to keeping your online services secure. Craving more insights on buffering your site from these cyber terrors? Flip through our article on dedicated server hosting for e-commerce.
In-depth Look at DDoS Attacks
Understanding Botnets
Ever noticed when the internet just stops altogether? That could be a DDoS attack in action! It’s like a digital dogpile where a gang of hijacked gadgets—think computers, phones, even toasters—team up to knock down a single target.
These armies called botnets, amp up the chaos, hurling oceans of data at whatever they’re going after, making them a weapon of choice. The wild part? You can rent these botnets out, kind of like a ruthless AV club, increasing the chaos and making it everybody’s problem.
Signs of a DDoS Attack
Spotting a DDoS attack can feel like finding a needle in a haystack, but there are tell-tale signs. Suddenly, your go-to website or service slows to a crawl or vanishes altogether—it’s like rush hour traffic hits your network. The trick is to dig into those clues with traffic analytics tools, identifying the rogue waves in the flood:
- Randomly high traffic from all corners of the web.
- Spikes in usage at those midnight hours when things should be chill.
- Repeated hits on one particular page or endpoint.
- Network traffic doing a weird tango (Cloudflare).
Common Symptoms of DDoS Attacks
| Symptom | Description |
|---|---|
| Slow Network Performance | Your favorite site turns into a turtle. |
| Increased Spam Emails | An avalanche of junk mail lands in your inbox. |
| Service Unavailability | Access to your website is like a mirage. |
| Unusual Traffic Patterns | Traffic movements that look straight outta sci-fi. |
Mitigation Strategies
Fighting off DDoS attacks needs some tactical planning, especially when your website is chillin’ on dedicated server hosting with DDoS protection. Here’s how to beef up your defense line:
- Traffic Filtering: Think of it as an internet bouncer—only allowing the cool crowd (legit traffic) into the club while chucking out the rowdy ones.
- Rate Limiting: Puts a cap on how often a single IP can pester you, slashing anyone jerk’s potential for harm.
- Network Traffic Monitoring: Keep eyes peeled on network movement, detecting weird blips before things get gnarly. Have a peek at our network traffic monitoring guide.
- Content Delivery Networks (CDNs): Imagine a squad of mini-servers sharing the load, giving you more shoulders to handle a DDoS hit, all while stealthily caching stuff near the users.
- Web Application Firewalls (WAFs): Like the digital knight, halting dubious traffic from getting too comfy on your server. Dig deeper with our Web Application Firewalls article.
For top-tier shielding, cast your net wide over DDoS protection services like AWS Shield, Cloudflare, and Imperva DDoS Protection. Fortifying your server hosting with solid DDoS armor can seriously bulk up your defenses against these cyber nuisances.
Check out our tips on Best Practices for DDoS Protection and dive into managed dedicated server hosting for that extra layer of security. Always think about your server hosting setup when lining up these strategies, ensuring you’re not caught napping.
Benefits of Dedicated Server Hosting
Picking the right hosting option is no joke when you want your business to run smoothly and safely. Dedicated server hosting steps up with some killer benefits, especially when it comes to security and handling resources. Here’s what’s cool about it:
Supercharged Security
Dedicated server hosting amps up security, and it’s like having your own private bodyguard for busy websites and critical data. Shared servers? Nah, they’re like a crowded bus with everyone sharing the same ride. Dedicated servers, however, give their all to just one client. This means they stand strong against online bullies like DDoS attacks.
With all resources focused on one client, you get to use top-notch security tools like firewalls and intrusion detectors. For the inside scoop on keeping your server safe, check out these security best practices.
Tailored DDoS Protection
When it comes to handling DDoS nasties, dedicated servers let you suit up specifically for your business’s needs. Tailor-made DDoS protection ensures you’re covered from all angles, even the sneaky ones. Pros like GCore offer layered defenses, fighting off bad guys at all network levels. They even throw in real-time bot shielding and next-gen firewalls to smack those threats down fast. Wanna know who else is in the game? Here’s a peek at the best enterprise-focused dedicated hosting services.
| Provider | DDoS Defense Layers | Unique Perks |
|---|---|---|
| GCore | L3, L4, L7 | Bot busting, cool firewalls |
| Vercara UltraDDoS | Multi-layer, 12+ Tbps | World-wide data cleaning, backyard hardware |
| Cloudflare | L3, L4, L7 | Global teamwork, zip-fast CDN auto-routing |
All-In Resource Allocation
Here’s the big win: all server guts—bandwidth, CPUs, memory—are fighting the DDoS fight for you on a dedicated server. No sharing means when an attack hits, you stay standing tall and fast, even if the net is going nuts. This is major for places pulling in lots of visitors, like web stores and banks. Get more smarts on knowing when you need to switch to a dedicated server.
| Attack Size | Shared Defense | Dedicated Defense |
|---|---|---|
| Small DDoS | Meager resources | All you got |
| Big DDoS | Prone to crashing | Ironclad and ready |
Choose dedicated server hosting to boost your security strategy, whip up custom DDoS shields, and rally all resources when things get thorny. Crank your server’s strength with upgrades like CDNs and WAFs.
For the dollars and cents breakdown, swing by our hosting cost guide. If you’re making the leap, peek at our migration tips to do it like a pro.
Leading DDoS Protection Services
Picking the right shield for your dedicated server hosting adventures can make or break your online safety. Here’s a lineup of top-notch DDoS protection services that’ll help keep the digital baddies at bay.
AWS Shield
Amazon’s AWS Shield is like having a bodyguard for your apps on the AWS stage; it’s all about defending against those not-so-friendly network and transport layer thugs. With its always vigilant detection and quick-to-act inline rescue measures, AWS Shield works tirelessly to keep your apps running smoothly without hiccups.
Key Features:
- Constant watchfulness
- Swift inline countermeasures
- Defense against network and transport mischief
| Feature | Description |
|---|---|
| Detection | Ever-watchful |
| Mitigation | Swift and inline |
| Attack Layers | Network, Transport |
Want to know more about hosting and shoring up your defenses? Check out this guide on best dedicated server hosting.
Cloudflare
Cloudflare struts its stuff with a cloud-based DDoS bouncer that’s all about covering every angle—from layer 3 to layer 7. Unlike those bulky hardware fellows, Cloudflare’s global posse chips in with DDoS defense, ensuring websites, apps, and networks are safely tucked under its wing.
Key Features:
- Global team effort in DDoS defense
- Multi-layer coverage
- Protects websites, apps, and networks
| Feature | Description |
|---|---|
| Mitigation Scope | Global reach |
| Attack Layers | Multi-layer (7, 3, 4) |
| Focus | Websites, Apps, Networks |
Peek into how Cloudflare can boost your server’s mojo in our article on optimizing dedicated server performance.
Imperva DDoS Protection
Imperva steps up with heavyweight DDoS mitigation, flaunting a cool three-second response time for any pesky attack. It comes with a fast, no-sweat setup, ready-made policies, smart self-tuning, and sharp analytics. Industries like gaming, healthcare, and tech have found their match here.
Key Features:
- Serious DDoS mitigation muscle
- Blink-and-you’ll-miss-it 3-second response
- Ready policies and brainy self-tuning
| Feature | Description |
|---|---|
| Mitigation Time | Lightning-fast 3 seconds |
| Policies | Ready to roll |
| Tuning | Adaptive intelligence |
Get savvy with security via our deep dive on dedicated server security measures.
GCore DDoS Protection
GCore Labs brings the heat with a multi-layered defense squad for your dedicated servers. You get real-time traffic wizardry, automatic snoop-spotting, and fast-action countermeasures against attack. GCore ensures you’re ready for all kinds of DDoS trouble, making it a solid pick for high-stakes settings.
Key Features:
- On-the-spot traffic insights
- Auto-detect and react in a flash
- Guards against every type of DDoS villain
| Feature | Description |
|---|---|
| Traffic Analysis | Real-time vigilance |
| Detection | Auto-alerts |
| Protection Scope | Every kind of attack |
See what makes the best server choice in our dedicated server configuration guide.
Picking the right DDoS protector is crucial for your digital domain’s peace of mind. Need tips on choosing wisely? Dive into our insights on dedicated server security best practices and hosting with primo support.
Integrated DDoS Protection Features
Auto-Updates and DDoS Protection
Keeping your dedicated server secure is kinda like making sure your car gets its oil changed on time – just way more digital. Auto-updates for your server are essential to lock those sneaky cyber gremlins out. Hosting companies, like the kind folks at InMotion Hosting, have you covered with their automatic updates and Corero DDoS protection.
This Corero system is like your server’s bouncer, spotting troublemakers before they cause a ruckus. It specializes in spotting and stomping out DDoS threats, keeping your server’s performance steady. Thanks to its almost-instant spywork, nearly all the vulnerabilities are dust. That’s peace of mind for businesses running tight online ship.
For those managing bustling websites, or mission-critical apps, these automated defenses crank up your protection game to lock down emerging threats.
DDoS Mitigation Techniques
Think of tackling DDoS as a cake made of layers – because you need a multi-layered approach to really save the day. Here’s your recipe:
- Rate Limiting: Limits how many requests a server can handle so it doesn’t get swamped.
- Web Application Firewalls (WAF): Acts like traffic police, supervising what comes and goes online.
- Traffic Analysis: Sniffs out funky traffic that signals trouble, ensuring a quick call to action.
- Redirection: Redirects malicious traffic to a cleansing center to wash off nasty bits before they reach your server.
Big names like AWS Shield and Imperva employ these strategies. AWS Shield is like your digital guard dog, staying alert and handling threats. Meanwhile, Imperva is all about rapid response, with an express three-second fix.
Cloud-Based vs. Dedicated Protection
Picking DDoS protection for your server? You’ve got options: cloud to the rescue or dedicated and dialed in. Here’s the scoop.
Cloud-Based Protection:
- Perks: It’s scalable and won’t break the bank. Plus, it’s got a long reach across data zones. A player like Cloudflare can squish a massive DDoS like it ain’t no thing – think 71 million asks per second handled.
- Examples: AWS Shield, Imperva, Vercara UltraDDoS Protect.
- Downside: Might slow things a tick if far-off centers are cleaning up traffic.
Dedicated Protection:
- Perks: Offers supreme control and hack-busting power. Fast-acting pros like Corero keep latency low and threats checked.
- Examples: On-site tools such as Vercara can handle minor problems solo and call on cloud help for the biggest messes.
- Downside: Higher up-front costs and trickier to manage, only as strong as its hardware.
| Protection Type | Benefits | Examples | Drawbacks |
|---|---|---|---|
| Cloud-Based | Scalable, Affordable, Wide reach | AWS Shield, Cloudflare, Imperva | Possible Lag |
| Dedicated | High Performance, Full Control | Corero, Vercara | Costly, Complex Setup |
The right DDoS protection choice? It’s all about matching these features with what your biz needs. Check out our best dedicated server hosting for more tips on nabbing a perfect server combo for a busy site. Looking for deeper understanding? Peek at our thorough dedicated server hosting guide.
Best Practices for DDoS Protection
Want to avoid sleepless nights worrying about DDoS attacks? Then let’s chat about some smart ways to beef up your defenses. Grab a coffee, and keep reading for crucial strategies that’ll help you protect your dedicated server hosting like a pro.
Content Delivery Networks (CDN)
Picture a CDN like the bouncer at a club—only letting in the right kind of crowd and tossing out the troublemakers. Using a Content Delivery Network partnered with specialized DDoS fighters keeps your traffic flow smooth. CDNs juggle site traffic across several servers, kicking out the bad guys before they crash your party. High-traffic sites and e-commerce hubs particularly love this setup for its chill approach to chaos control.
| CDN Goodies | Why They’re Awesome |
|---|---|
| Traffic Juggling | Shuffles traffic around to balance server loads |
| DDoS Muscle | Spotlights and shuts down malicious traffic |
| Speed Boost | Cuts down on lag and wait times |
Get more scoop on CDNs with dedicated server hosting for e-commerce.
Web Application Firewalls (WAF)
Think of a WAF as your digital security guard, laser-focused on sniffing out and squashing threats like dodgy XSS scripts, evil SQL injections, and other baddies from the infamous OWASP Top-10 list. With tailored security options, a WAF does more than a run-of-the-mill firewall, offering customized protection to fit your specific needs. That’s fintech, healthcare, and cloud services’ best friend right there.
| WAF Goodies | Why They’re Awesome |
|---|---|
| Bad Guy Detector | Sniffs out and knocks back common cyber threats |
| Custom Defense | Set security rules that fit your needs |
| Insta-Guard | Watching and blocking threats 24/7 |
Get clued up on security must-dos in dedicated server security best practices.
Network Traffic Monitoring
Staying ahead of DDoS attacks is all about keeping an eye on the road. With round-the-clock traffic monitoring, gathering data, and breaking down logs, you’ll be the first to spot funky behavior and nip potential terror in the bud. Perfect for enterprises, gaming giants, and media moguls looking to stay on top of their game and protect their turf.
| Monitoring Perks | Why They’re Awesome |
|---|---|
| Speedy Alerts | Quickly spots any suspicious traffic blips |
| Data Dive | Gives you solid intel for shoring up defenses |
| Nonstop Vigilance | Keeps watch around the clock for lurking threats |
Need more on keeping an eagle eye on your network? Stop by to optimize dedicated server performance.
By folding these practices into your routine, you’ll not only amp up your defense against tech headaches but also keep your dedicated server running like a dream. Don’t stop here—check out the best dedicated server hosting and top tips on how to secure your dedicated server.
Conclusion
In conclusion, dedicated server hosting integrated with robust DDoS protection remains the cornerstone of secure online operations.
This guide has outlined how multi-layered defenses—ranging from traffic filtering and rate limiting to sophisticated firewall implementations—play a pivotal role in neutralizing volumetric, protocol, and application-layer attacks.
By evaluating providers on criteria such as experience, scalability, and customer support, businesses can select a solution that guarantees not only superior performance but also uninterrupted service during cyber onslaughts.
The discussion also highlights the importance of addressing emerging vulnerabilities in IoT devices and the advantages of leveraging a hybrid security model that combines dedicated hardware with cloud-based solutions.
Adopting these best practices will empower your infrastructure to combat threats proactively, maintain data integrity, and uphold your reputation.
Ultimately, investing in enterprise-grade DDoS protection ensures that your dedicated servers remain resilient, secure, and capable of supporting your business growth in an increasingly hostile cyber environment.
FAQs
What is dedicated server hosting?
Dedicated server hosting provides exclusive access to server resources, enhancing performance and security by eliminating resource sharing.
How does DDoS protection work?
DDoS protection mitigates attacks by filtering out malicious traffic through techniques like rate limiting, traffic filtering, and real-time monitoring.
What are the benefits of cloud-based vs. dedicated DDoS protection?
Cloud-based solutions offer scalability and wide geographic coverage, while dedicated protection provides greater control and lower latency.
How do I choose the right DDoS protection provider?
Evaluate providers based on their experience, range of protection services, scalability, integration capabilities, cost, and quality of customer support.
What are the best practices for maintaining dedicated server security?
Implement multi-layered defenses such as CDNs, WAFs, continuous network monitoring, regular software updates, and strong network segmentation.
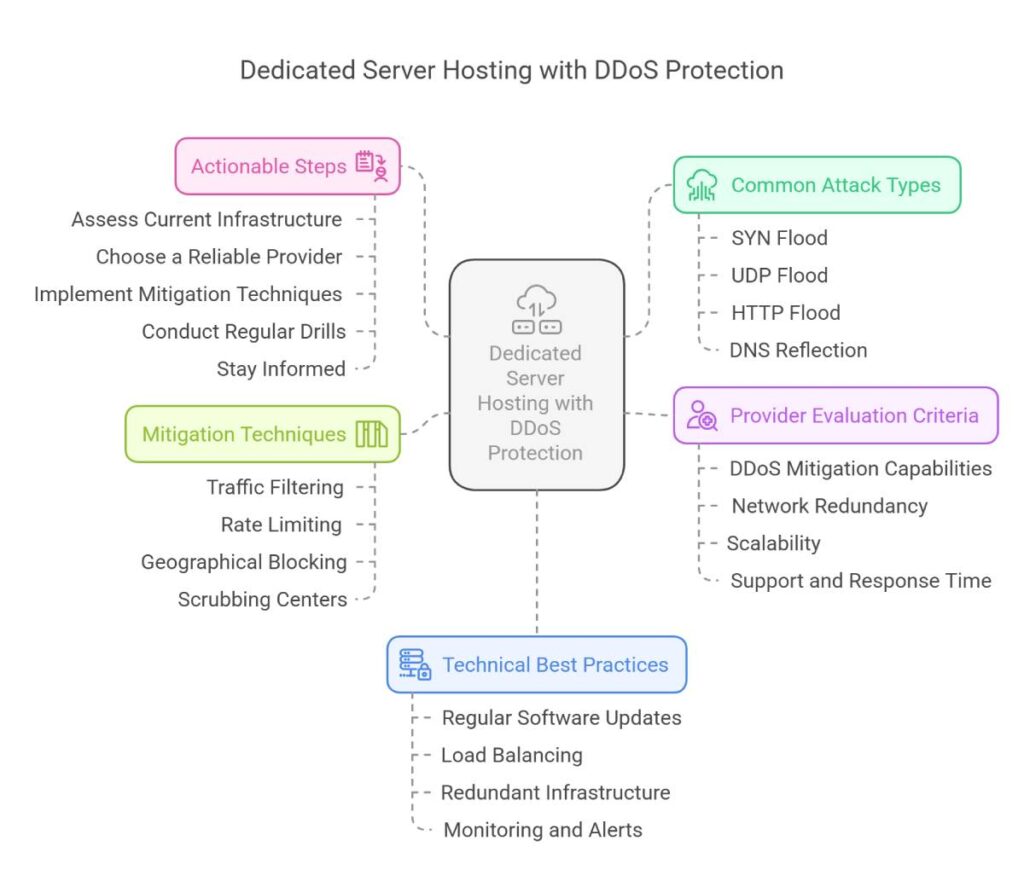
Technical Best Practices
- Regular Software Updates: Keep all server components and security patches current.
- Multi-Layered Defense: Utilize a combination of CDNs, WAFs, and real-time traffic monitoring.
- Network Segmentation: Isolate critical resources to limit the impact of attacks.
- Automated Updates & Alerts: Implement auto-updates and real-time alert systems for prompt threat response.
- Comprehensive Auditing: Regularly perform vulnerability assessments and penetration tests.
- Data Backups: Maintain frequent backups to ensure quick recovery after an incident.
Recommended Hosting Tools and Solutions
- AWS Shield: Comprehensive DDoS protection for AWS-hosted applications.
- Cloudflare DDoS Protection: Global defense with multi-layer security.
- Imperva DDoS Protection: Rapid response with adaptive, real-time mitigation.
- GCore DDoS Protection: Advanced traffic analysis and automatic threat detection.
- Vercara UltraDDoS Protect: Hybrid hardware and cloud-based defense.
- Corero DDoS Protection: High-performance on-site mitigation solutions.
- InMotion Hosting & Liquid Web: Leading providers of dedicated server hosting.
- CDN Solutions: Akamai and Cloudflare for distributed content delivery.
- WAF Solutions: ModSecurity and Barracuda Web Application Firewall for tailored protection.
This comprehensive enhancement integrates enterprise-level SEO techniques with actionable insights and technical accuracy—ensuring your audience receives both value and confidence in your hosting solutions. Enjoy your elevated content!


